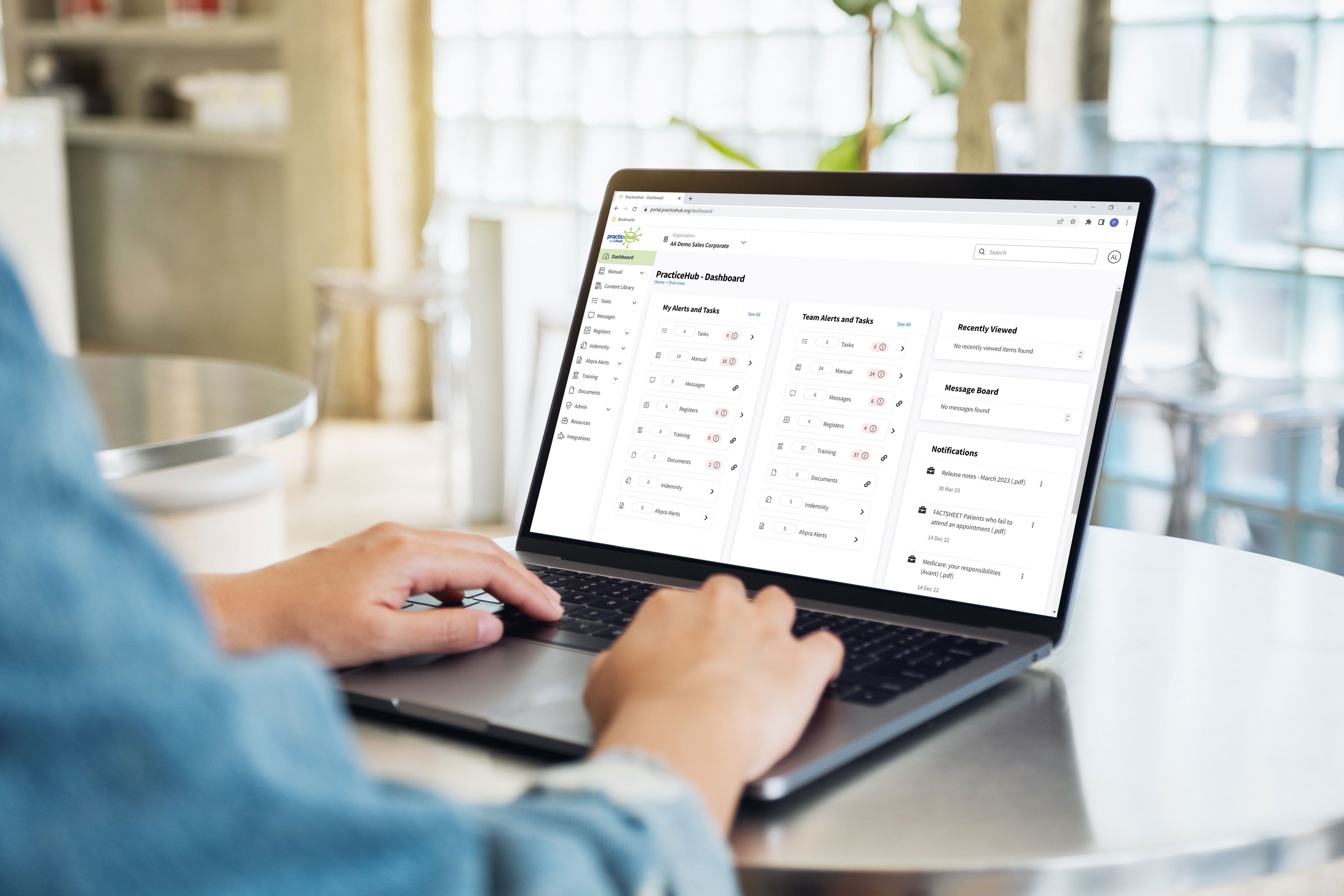
PracticeHub Platform
PracticeHub helps to reduce administration and compliance burdens of running a healthcare business. Whether you are a general practice, specialist clinic, pharmacy or allied health provider – PracticeHub can help you take control of the business administration and compliance areas that are time consuming and management intensive.
According to an independent evaluation, practices using PracticeHub saved between $4,600 and $9,200 compared to non PracticeHub users.*
"Management Support
Risk Management
Human Resource Management
Accreditation

What is PracticeHub?
Jo Kruger, Operations Support & Improvement Manager, at Ochre Health shares her experience with using PracticeHub, and how the ability to document policies and procedures, prepare for accreditation and personalised training and compliance modules within the platform have benefited the team at Ochre Health.

Effortless quality management
Streamline and safeguard your practice with a digital platform designed to drive efficiency, protection and growth.
Efficiencies in management support costs
Realised through access to current and critical information, all in one place, accessible anytime and anywhere.
Fast track and safeguard compliance documentation
Utilise our extensive Content Library and Training modules, with ready-to-use content you can trust, to save time, reduce risk, support compliance and operational excellence.
Manage and monitor compliance
Help your team stay current and compliant with set and forget review and compliance schedules, intuitive workflows, and notifications to keep everyone informed.
Reduce operational risk
Centralising and managing your practice policies, procedures, and related documentation with PracticeHub.
Health professional credentialing made easier
Save time and stay up to date with real-time alerts delivered to you for changes to your health practitioner’s Ahpra registration status.
Features
| PracticeHub Features | |
| Manual & Content Library | Your single source of truth for policies and procedures to run your business, accessible anytime and anywhere. Stay current with legislative changes and save time with our expertly written and ready to use content aligned with health industry standards and guidelines designed specifically for healthcare businesses. |
| Document Management | Centralised online platform with unlimited storage, upload, preview, and download document capabilities, supported by audit trail functions that automatically track changes, and comprehensive search capabilities so you and your team can quickly and easily find what you need, when you need it. |
| Quality Registers | Managing risk is everybody’s responsibility. Streamline the capture, monitoring and management of feedback, incidents, and risks easily both within and outside of PracticeHub. With configuration capabilities to meet your specific needs, Quality Registers helps to support and promote quality improvement in healthcare organisations. |
| Custom Registers | Reduce the reliance on external systems by designing and creating what you need with Custom Registers, a new way to structure, organise and connect information for your organisation. Use our out-of-the box templates or create your own register in less than 1 minute. |
| Contracts, Insurance and Equipment Registers | Record and manage important business details for equipment, key supplier contracts and insurances in one place. Set reminders for key dates such as equipment maintenance and insurance renewals. |
| Dashboard, Notifications & Message Board | Promote awareness, transparency and accountability for you and your team with a range of in-platform communication capabilities including a comprehensive dashboard with easy to see alerts, in-platform and email notifications, and message functions. |
| Health Professional Credentialing | Reduce the burden of managing and monitoring the indemnity and Ahpra registration status for your health professionals. Regular and automated updates save you time, reduce risk and give you peace of mind. |
| Team Medical | Access preferential pricing for medical consumables and monitor spending with our Team Medical Dashboard. Make informed decisions with budget tracking functions, and easily view your year-on-year comparative spending and saving patterns in one place. |
| Training Courses | Increase your team’s knowledge while complementing the compliance process with our in-built training courses targeting key topics including Privacy and Confidentiality and Organisational Culture. |
| Tasks Management | Is your To-Do list never ending? Support consistent and timely delegation of important business activities with our task management module. Easily track assignment, status, and completion with our tasks management module. |
| Resources | Need a template for that? Our Resources module gives you access to a range of templates and documents for key business activities like meeting agendas and position descriptions. Save time and let us support you and your business today. |
Disclaimers
*Larter report: Economic evaluation to ascertain the return on investment for general practices using PracticeHub. If you would like to view this report, please contact us at practicesolutions@avant.org.au
Persons implementing any recommendations contained on this webpage must exercise their own independent skill or judgment or seek appropriate professional advice relevant to their own particular practice. Compliance with any recommendations will not in any way guarantee discharge of the duty of care owed to patients and others coming into contact with the health professional or practice. Avant and Avant Practice Solutions are not responsible to you or anyone else for any loss suffered in connection with the use of this information. Information is only current at the date initially published. © Avant Mutual Group Limited 2024.



